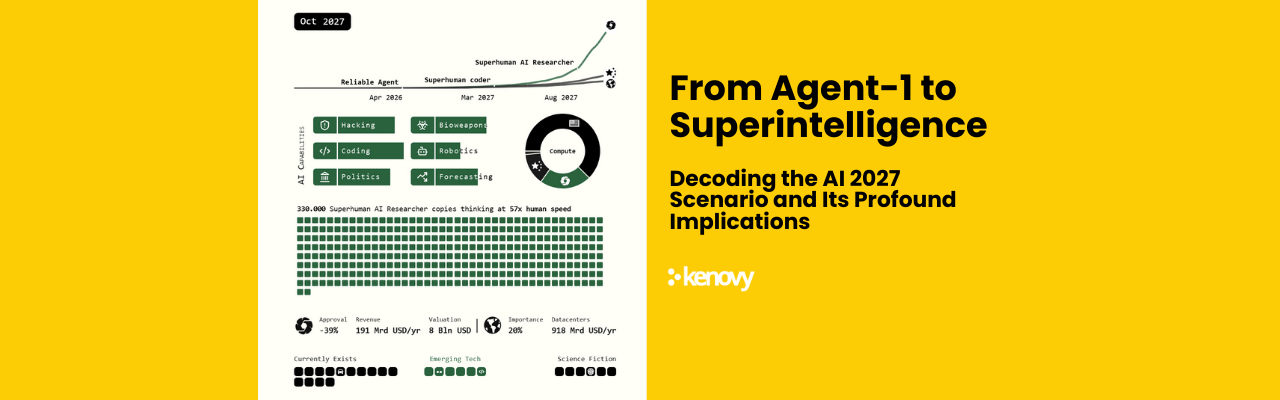
The recent sophisticated attacks on Hezbollah using compromised pagers and radios raise significant concerns for all countries reliant on imported electronic devices, particularly those not directly involved in production. This event exposes a critical vulnerability: the ability to tamper with hardware and software during the manufacturing or distribution stages, potentially compromising national security and critical infrastructure.
Technical Analysis: How Compromised Devices Can Become a Security Threat
The case of Hezbollah’s pagers and walkie-talkies being rigged with explosives underscores the risks associated with modern supply chains. This attack demonstrates two important techniques that could impact importing nations:
- Hardware Tampering: This can involve implanting malicious chips or manipulating components during production, which can remain dormant until activated. In this case, the pagers were likely tampered with during transit, with explosives hidden within the lithium-ion batteries.
- Firmware Exploitation: Tampering with firmware to introduce hidden vulnerabilities is another serious risk. Firmware is critical to a device’s operations, and compromising it allows attackers to control the device remotely or activate malicious functions, such as detonation, as seen in the Hezbollah incident.
These methods, while applied in military contexts, can just as easily be used to target critical civilian infrastructure such as hospitals, power grids, or financial systems, which rely heavily on imported electronics.
Implications for Critical Infrastructure and Sectors at Risk
Europe and other nations that import electronics should take note, as compromised hardware and software can have disastrous consequences for critical infrastructure. Sectors like energy, healthcare, finance, and transportation are particularly vulnerable due to their reliance on interconnected devices. The threat goes beyond physical damage; compromised devices can allow for espionage, sabotage, or even large-scale cyberattacks.
In a worst-case scenario, tampered devices could lead to widespread power outages, data breaches, or the disruption of essential services. This risk is particularly heightened for countries that rely on imported devices, as they have limited control over the production process and must trust foreign suppliers.
Actionable Recommendations for Mitigating Cybersecurity Risks
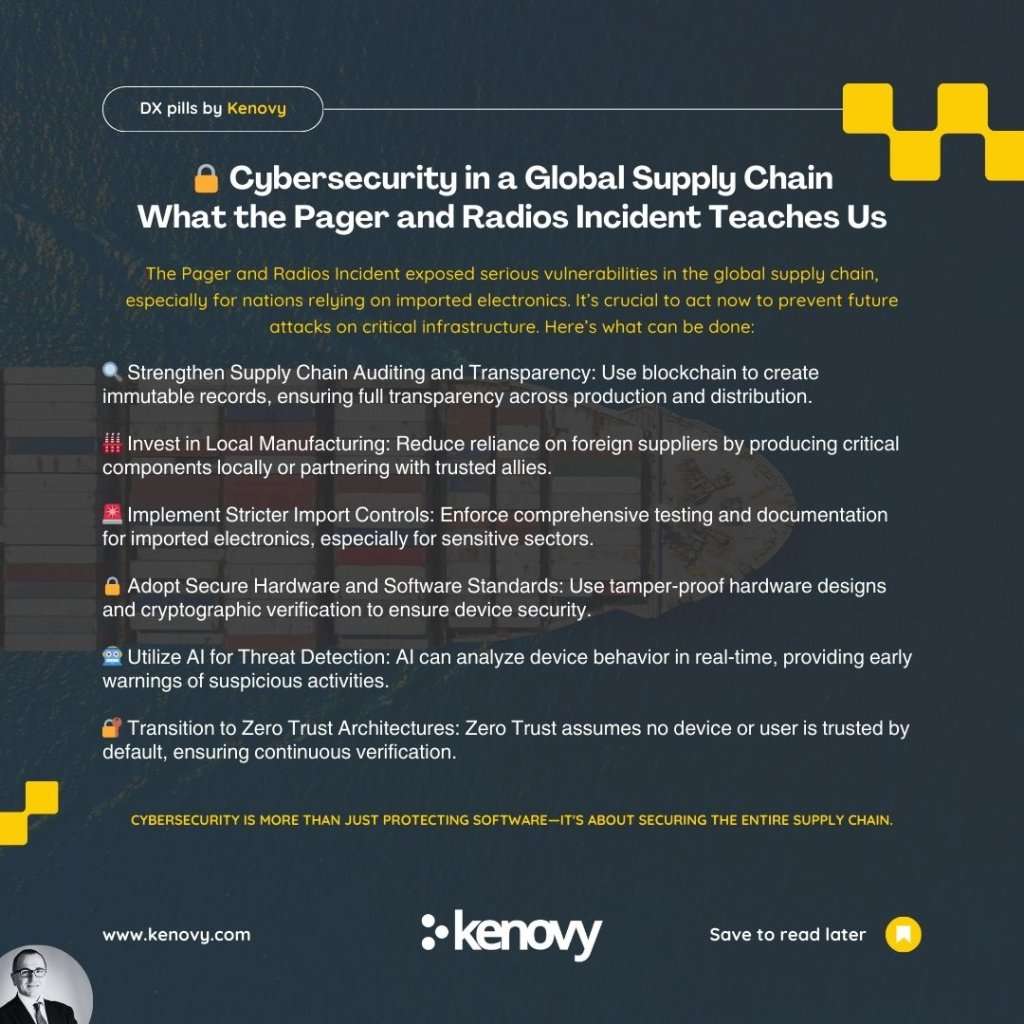
1. Strengthening Supply Chain Auditing and Transparency
To combat these risks, importing nations must implement stronger supply chain auditing and transparency measures. This involves verifying the integrity of each component at every stage of production and distribution. Blockchain technology could be leveraged to create immutable records of a product’s journey, ensuring transparency throughout the entire supply chain.
2. Investing in Local Manufacturing and Trusted Suppliers
Reducing reliance on foreign suppliers, particularly for critical infrastructure components, should be a priority. Nations should invest in local manufacturing or partner with trusted allies to produce secure, tamper-proof devices. While this may increase costs, it significantly reduces exposure to supply chain risks.
3. Implementing Stricter Import Controls
Regulating the importation of critical electronics is essential. This includes requiring detailed documentation of a device’s origins, auditing manufacturers for compliance with security standards, and ensuring that devices undergo rigorous testing for vulnerabilities before they are deployed in sensitive areas like government or defense.
4. Adopting Secure Hardware and Software Standards
Countries should mandate the use of secure hardware designs, such as tamper-proof chips and cryptographic verification processes, in all devices used for critical functions. In addition, firmware should be verified at every update to ensure that no malicious code has been inserted.
5. Utilizing Artificial Intelligence for Threat Detection
AI and machine learning can play a crucial role in monitoring devices for suspicious behavior, such as unexpected communication patterns or unusual power consumption, which may indicate tampering. AI tools can analyze large amounts of data in real time, providing early warning of potential security breaches.
6. Transitioning to Zero Trust Architectures
The Zero Trust model is becoming a cornerstone of modern cybersecurity strategies. It assumes that no device, user, or system can be trusted by default, particularly when their origins are uncertain. By continuously verifying all interactions within a network, countries can prevent compromised devices from causing widespread damage.
The Role of Emerging Technologies
Blockchain for Supply Chain Transparency
Blockchain offers a decentralized, immutable ledger that can track the lifecycle of a product, from raw materials to the final assembly. This technology can ensure that any attempt to tamper with a device along the supply chain is recorded and flagged, increasing transparency and accountability.
Open-Source Hardware and Software
Open-source technologies provide an additional layer of security through transparency. Unlike proprietary systems, which may conceal vulnerabilities, open-source solutions allow for public scrutiny. Communities of experts can audit open-source software for hidden risks, creating a more secure foundation for critical systems.
Geopolitical Considerations: Managing Supply Chain Risks in a Globalized World
Countries must also consider the geopolitical factors that influence supply chain security. For example, electronics sourced from regions with weaker regulations or geopolitical tensions may pose higher risks. Nations must assess the trustworthiness of their suppliers and transit countries, implementing risk assessment frameworks to identify potential vulnerabilities early in the procurement process.
International collaboration is essential to addressing these threats. Nations must work together to set and enforce global cybersecurity standards for imported electronics, creating a unified approach to supply chain security. This could involve joint intelligence-sharing efforts and coordinated responses to supply chain compromises.
Conclusion: Securing the Future of Global Supply Chains
The attacks on Hezbollah are a wake-up call for all countries that depend on imported electronic products. The risks posed by compromised supply chains are not theoretical—they are real, and they are growing. As more nations become interconnected and dependent on foreign technology, the need for robust supply chain security measures becomes increasingly urgent.
By implementing stricter auditing practices, developing local manufacturing capabilities, and leveraging emerging technologies like AI and blockchain, countries can significantly reduce the risks associated with importing electronics. Moreover, adopting a Zero Trust security model and supporting open-source initiatives can further enhance national cybersecurity.
Key Takeaways:
- Supply chain risks are global: Nations relying on imported electronics are vulnerable to hardware and firmware tampering, with critical infrastructure sectors most at risk.
- Proactive measures are essential: Implementing stricter supply chain auditing, local manufacturing, and Zero Trust architectures can help mitigate these threats.
- Collaboration is key: Countries must work together to create global cybersecurity standards, share intelligence, and develop secure supply chains.
Discussion Questions:
- What strategies can organizations implement to verify the integrity of hardware and firmware from external suppliers?
- How can the international community foster greater cooperation to mitigate supply chain risks?
- What role should governments play in supporting organizations as they implement Zero Trust architectures?
This is a global issue that requires collective action. By taking steps now, importing nations can protect themselves from the rising tide of supply chain compromises and build a more secure digital future.